Cybersecurity news and analysis

Cybersecurity breaches are threats that all companies are at risk. Why not-studies show that by the end of 2021, cybercrime is expected to cost the world $3 trillion. Also, companies that have become victims of cyber-attacks increase steadily every year. But what are cybersecurity breaches anyway? SEE ALSO: Your boss
As a huge number of people work from home during the COVID-19 crisis, Zoom videoconferencing is thriving. Here are some common-sense guidelines that should be followed to safely host public meetings on Zoom without being interrupted by uninvited attendees. Creating a meeting on Zoom When creating a meeting, consider t

A barrage of privacy and security incidents has now landed Facebook in troubled waters again. Privacy regulators in Canada have determined that Facebook broke local privacy laws by mishandling user data. The social media giant might have to cough up $3 - $5 billion as fines imposed by the Federal Trade Commission (FTC)

An unauthorized person gained access to a Docker Hub database that exposed sensitive information for approximately 190,000 accounts (less than 5% of Hub users). Data includes usernames and hashed passwords for a small percentage of these users, as well as Github and Bitbucket tokens for Docker autobuilds. Note: Gi

The European Commission and the Austrian Ministry for Transport, Innovation and Technology cordially invite you to participate in the 2018 Security Research Event (SRE) taking place on 5th and 6th of December 2018 in Brussels at the Square Meeting Centre. Your browser does not support the video tag. Conference ove

Protecting sensitive data is the end goal of almost all IT security measures. Two strong arguments for protecting sensitive data are to avoid identity theft and to protect privacy. SEE ALSO: Facebook loses control of over 50 million users data The more valuable the information in your database, the more likely it is t

If you have used Facebook apps on earlier versions of Android phones, then most likely, the social network has been logging your phone calls and personal messages. SEE ALSO: Can you predict who will win the US election? After Facebook lost control of over 50 million users' data many of its users have deleted their acc

The issue of using posts, comments or personal messages on social media to predict the probability of electing a candidate during presidential elections is not new. Previously I have been sharing my experience with you on this. SEE ALSO: Can you predict who will win the US election? It only generated a huge buzz when

Last year Microsoft Corp. closed its roughly $26 billion deal to buy professional-networking site LinkedIn, cementing the largest acquisition in the tech giant's history. But few people may know that business valuation is a process to determine what a business is worth by looking at the facts, including the one that L

On Tuesday, the UK's National Crime Agency (NCA) has reportedly arrested a 20-year-old man who is suspected to be a member of the group calling itself the Turkish Crime Family. The group recently gained media attention after trying to blackmail Apple for $75,000 in crypto-currency. SEE ALSO: Apple increases iCloud sec

If you use iCloud to sync your Apple devices, your private data may be at risk of getting exposed or deleted by April 7th. SEE ALSO: Hacking People While Walking Around in Public The hacker group, who identified themselves as "Turkish Crime Family", is threatening Apple to remotely wipe data from those milli

Activities in cyberspace during Four-day war (April, 2016). Attack April 2, 2016 Government & media The hacker group “MMCA” (formerly known as Monte Melkonian Cyber Army) targets DoS/DDoS attacks on Azerbaijan government and media websites: Gov.az Aze.az Apa.az Internet Service Providers The hacker group “MMCA”

Cloudflare, a multibillion-dollar startup that runs a popular content delivery network used by more than 5.5 million sites, accidentally leaked customers' sensitive information for months. Last Friday, Tavis Ormandy from Google's Project Zero contacted Cloudflare to report a security problem (the flaw was dubbed Cloud

Pwnie Express released its yearly industry report: Internet of Evil Things, providing insight on products that the IT professionals should be wary of. Your browser does not support the video tag. According to Pwnie Express research: 66% don't know or aren't sure how many connected devices their colleagues bring

Who would win the battle for the White House to become the next President of the United States was a topic of hot debate in 2012. Much of that debate was taking place online, with plenty of people blogging, tweeting or updating social media with their thoughts on Mitt Romney versus Barack Obama. Photo: usatoday.com Th

I have read an interesting article in our partner's website recently about an employer who read the employee's messages to make sure she is not doing anything else rather than her regular job at the office. Photo: xervant.com In the article you will find detailed information about the legal aspects of such incident, s

Have you ever wondered how much is your email password worth? It depends what data are you trying to protect in electronic form using that password. John Brennan, Director of the Central Intelligence Agency (Photo: boingboing.net) Data security is a major issue for businesses and organizations today. That is why a gro

Symantec has detected up to 20,000 daily attempts to exploit a recently patched Joomla vulnerability that can be leveraged for remote code execution. Photo: www.tricountyweb.com The vulnerability, identified as CVE-2015-8562, was patched in mid-December with the release of Joomla 3.4.6 and hotfixes for versions 1.5 an
Passwords are a vital component used to access digital assets, that is why "Password Hygiene" is one of the highest priority requirements in large organizations. There are some common-sense guidelines that should be followed for a Good Password Hygiene to secure sensative data at work and in your pesonal lif

While education and efforts around online credentials are improving, password hygiene still has problems Image: Tested.com The Balance 60% of employees do work activities from a personal device 55% of employees do personal activities on work devices Continuous Mistakes One in three employees access work data from p

The number one cybersecurity startup on our list is Tanium, which raised over $190 million in 2015 for a new valuation of $3.7 billion, according to Pitchbook. A father-son duo, David and Orion Hindawi, founded the company and created its unique endpoint management system. At the latest valuation, they both became bill

The personal information of over three million Hello Kitty customers has been found online by security researchers. The database in question was found by security bod Chris Vickery and relates to the Japanese cartoon character's online community sanriotown.com, although those who registered accounts through hellokitty
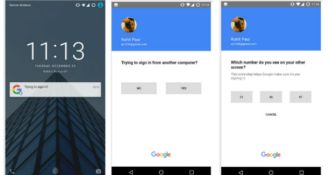
Google has confirmed that it's testing a password-free way to sign into a Google account. The approach allows users to authenticate by responding to a notification sent to their smartphones. It's no secret that passwords are the weak link when it comes to account security, with poor hygiene, credentials theft and hack

Twittor Twittor is a stealthy Python based backdoor that uses Twitter (Direct Messages) as a command and control server. Setup For this to work you need: A Twitter account (Use a dedicated account! Do not use your personal one!) Register an app on Twitter with Read, write, and direct messages Access levels. Install

Anonymous has admitted responsibility for a huge 40Gbps DDoS attack that took place last week on Turkish DNS Servers because Turkey is supposedly supporting ISIS/ISIL (otherwise known as Daesh). Anonymous claimed in its video to Turkey that the attack on the servers was part of their ongoing efforts to put an end to D
