WhatsApp remains one of the world's most widely used instant messaging (IM) platforms, serving more than two billion users globally. Its end-to-end encryption has long been positioned as a strong privacy safeguard, yet in practice, most real-world compromises in 2025–2026 do not target encryption itself. Instead, attackers focus on users, devices, and account-recovery mechanisms. This analysis examines the dominant WhatsApp hack threats observed today, explains why they persist, and outlines concrete protection strategies grounded in operational security best practices.

Understanding these threats requires looking beyond isolated technical flaws and examining how social engineering, identity abuse, and platform scale intersect to create systemic risk.
How WhatsApp Accounts Are Commonly Compromised
-
A majority of confirmed WhatsApp compromises stem from account takeover techniques, not cryptographic failure. One of the most prevalent vectors is one-time verification code phishing, where attackers trick users into sharing one-time registration (OTP) codes via SMS or voice calls. Once obtained, the attacker can register the victim's WhatsApp account on a new device, immediately severing access for the legitimate user.
-
Another growing threat is SIM-swap–assisted compromise. By fraudulently transferring a victim's phone number to a new SIM card, attackers intercept WhatsApp verification messages and password-reset flows. This technique is especially effective against high-value targets such as business executives, journalists, and public officials, where personal data is often publicly accessible.
-
In parallel, malicious QR-code abuse has increased. Users are lured into scanning fraudulent WhatsApp Web or "security check" QR codes, unknowingly granting attackers persistent session access. Because linked devices may remain active for long periods, detection is often delayed.
These attack paths share a common characteristic: they exploit trust, urgency, and user inattention rather than software vulnerabilities. As a result, purely technical defenses are insufficient on their own.
Wrong usage increases risk possibility
Quantitatively, WhatsApp's risk surface grows with usage intensity. Industry estimates indicate that active users check the app dozens of times per day, often responding quickly to messages without verifying sender authenticity. WhatsApp is increasingly used for sensitive personal communications with friends, informal task coordination with colleagues, and even for customer communications sharing private working files, despite not being designed as a secure data collaboration platform.
This behavioral reality amplifies risk. Attackers rely on speed and plausibility—posing as colleagues, managers, or service providers—to induce rapid responses. The more frequently a user relies on WhatsApp for real-time decisions, the higher the likelihood of successful manipulation.
Recommended Protection Measures and Why They Matter
Effective risk reduction requires layered controls applied at both individual and organizational levels.
For individuals
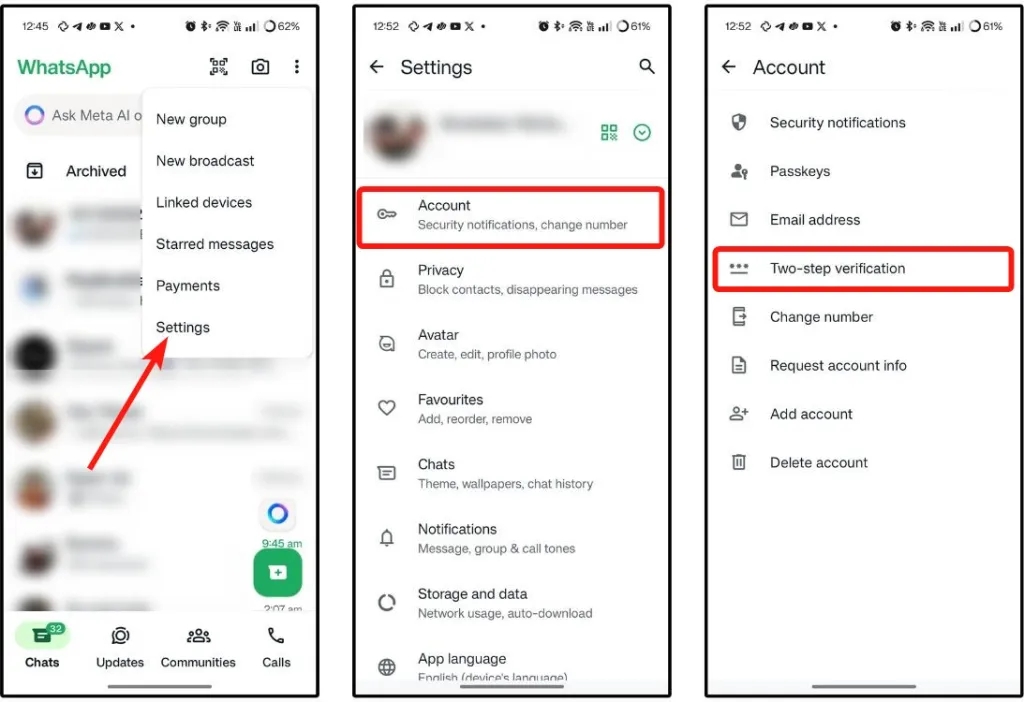
- Enable two-step verification (2FA) with a strong, unique PIN.
This adds a critical barrier against verification-code theft and automated takeover attempts. Without it, account recovery relies solely on possession of the phone number.
- Regularly review and revoke linked devices.
Persistent sessions are a favored attacker foothold. Periodic review limits the dwell time of unauthorized access as during reviews you may identify and remove unknown device linked to your account.
- Increase security awareness levels.
Training yourself to recognize urgency-based scams, impersonation cues, and unexpected verification requests is essential. Human vigilance remains the most effective control against social engineering.
- Restrict WhatsApp usage for sharing sensitive data.
Organizations should discourage reliance on consumer messaging apps for approvals, financial requests, or sensitive coordination, reducing the blast radius of compromise.
For Mobile Operators
Mobile operators play a decisive role because many attacks exploit telecom infrastructure, and can even be used to compromise online-banking accounts.
- Limit Access to SS7 Networks
Restrict SS7 network access exclusively to trusted and verified partners. Maintain a strict whitelist of authorized mobile network operators (MNOs) and signaling partners, and enforce strong access controls for any entity permitted to exchange SS7 messages. SS7 was built on implicit trust between operators. Unrestricted or weakly governed access allows malicious or compromised networks to inject signaling messages that enable SMS interception, call redirection, and subscriber location tracking. Limiting access directly reduces the attack surface and prevents abuse of legacy trust relationships.
- Choose and Maintain Reputable Interconnection Partners
Interconnect only with carriers and signaling partners that demonstrate mature security practices, including documented SS7 security controls, continuous monitoring, and incident-response capabilities. Reassess partner security posture regularly as part of interconnection governance. Many SS7 attacks originate from third-party or foreign networks rather than the victim's home operator. Even a well-secured carrier can be compromised indirectly through weaker partners. Careful partner selection and continuous reassessment reduce exposure to indirect signaling abuse.
- Deploy Advanced SS7 Firewalls and Intelligent Filtering
Implement advanced SS7 firewalls that inspect, validate, and filter all inbound and outbound signaling traffic. These systems should detect anomalies such as unauthorized location requests, SMS interception attempts, call forwarding manipulation, and malformed signaling messages. Manual monitoring cannot scale to the volume and complexity of SS7 traffic. Advanced firewalls provide real-time visibility and automated enforcement, allowing operators to block malicious signaling before subscribers are affected.
- Enforce Strict SIM-Swap Validation and Cooling-Off Periods
Require multi-factor identity verification for SIM replacement requests, including out-of-band confirmation and mandatory cooling-off periods before changes take effect. SIM-swap attacks are one of the most effective methods for bypassing application-level security. Strong validation and delayed execution reduce the success of social engineering attacks, especially when detecting SIM IMEI change assisiated to a mobile number.
- Enable SIM-Lock and Port-Out Protection by Default
Activate SIM-lock and port-out protection for all subscribers by default, requiring explicit and verified user approval to disable these safeguards. Default protections raise the barrier for attackers and reduce reliance on user awareness.
- Monitor, Log, and Correlate SIM-Swap and Signaling Suspicious Events
Continuously monitor SIM-swap activity and SS7 signaling events, correlating them with fraud indicators and account-takeover reports. Early detection dramatically limits impact and prevents prolonged unauthorized access.
- Coordinate with Application Providers and Regulators
Establish structured information-sharing channels with messaging platforms, financial institutions, and regulators. SS7 abuse and SIM-swap fraud are ecosystem-level threats that require coordinated response.
Conclusion
In 2026, WhatsApp security risks are best understood as identity and behavior problems, not data encryption failures. Attackers succeed by exploiting trust, convenience, and fragmented security practices across users and organizations. Mitigating these threats requires consistent use of built-in protections, strengthened mobile-identity security, and disciplined communication practices. Without these measures, even the strongest cryptography cannot prevent account takeover and downstream harm.