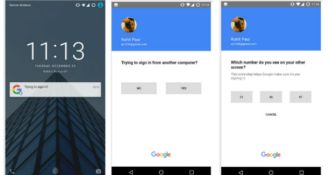
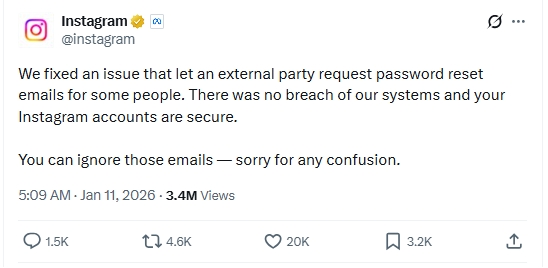
In January 2026, millions of Instagram users around the world were caught off guard after receiving unexpected password reset emails that they had not requested. The sudden influx of official-looking notifications sparked widespread concern about a potential data breach affecting one of the world's largest social media platforms. Subsequent investigations and official statements clarified that the incident was not the result of compromised user accounts or a breach of Instagram's core systems. Instead, it stemmed from a technical vulnerability that allowed third parties to trigger password reset emails without authorization. Meta, Instagram's parent company, confirmed that the flaw was quickly identified and patched, while emphasizing that user credentials remained secure.
 SEE ALSO: Common-sense Guidelines for a Good Password Hygiene
SEE ALSO: Common-sense Guidelines for a Good Password Hygiene
Password reset workflows are designed to notify users whenever a reset request is initiated, even if the request is unauthorized. This design choice prioritizes account activity transparency but can be abused if protective controls are insufficient. In this case, attackers were able to automate reset requests using publicly available identifiers such as usernames or email addresses, resulting in a flood of legitimate but alarming notifications. Importantly, the mechanism did not grant attackers access to accounts, change passwords, or bypass authentication safeguards.
Event chronology
- Instagram users globally received unsolicited password reset emails.
- Meta acknowledged a vulnerability that allowed external actors to trigger reset emails.
- The issue was patched, and no mass account takeovers were confirmed.
- Meta stated that Instagram's internal systems were not breached.
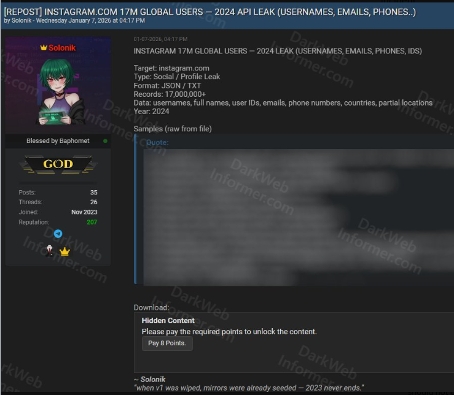
- A dataset advertised online allegedly contains approximately 17 million Instagram-related records.
- The dataset reportedly includes usernames, full names, user IDs, email addresses, phone numbers, countries, and partial location data.
Security researchers indicate the dataset is likely the result of scraping (web scraping) or aggregation from older sources rather than this vulnerability.
From a cybersecurity perspective, the presence of a large dataset containing personal identifiers does not automatically imply a system breach. The alleged 17 million-record dataset contains identifying and contact information, but critically does not include passwords. Such data, however, can still be weaponized for phishing, credential stuffing attempts using other breaches, or targeted social engineering. The coincidental timing of the dataset's circulation alongside the password reset incident amplified public concern, despite the lack of technical linkage between the two events.
What this means for Users
- Unexpected password reset emails do not automatically indicate a hacked account.
- The absence of passwords in the dataset significantly limits direct account takeover risk.
- Users should remain alert for phishing attempts using personal details.
- Enable two-factor authentication and verify reset actions only through official apps or URLs.
Conclusion
The Instagram password reset email incident illustrates how technical vulnerabilities and unrelated data exposure claims can converge to create widespread alarm. While Meta confirmed that no passwords were exposed or no systems were breached, the circulation of a dataset containing personal identifiers underscores the ongoing risks posed by data scraping and aggregation. Users and platforms alike must stay vigilant against evolving social engineering threats that exploit trust rather than technical compromise.